OpenID Connect relying party (developer) configuration
AppDirect marketplaces support the creation of OpenID Connect relying party configuration via the SUBSCRIPTION_ORDER event, similar to what is done with SAML.
📝 Note A single OpenID Connect client configuration (including client ID and secret) is created for each marketplace to which a Developer's products are distributed. This single client configuration is shared across all subscriptions in a given marketplace but returned for all SUBCRIPTION_ORDER events. For information on how to generate a client ID and secret, see Manage credentials.
The steps represented in the following flow chart are built on top of AppDirect’s standard Subscription event notification flow. Steps 5-10 represent the new steps that are required to support OpenID Connect SSO. A description of each step appears below the image.
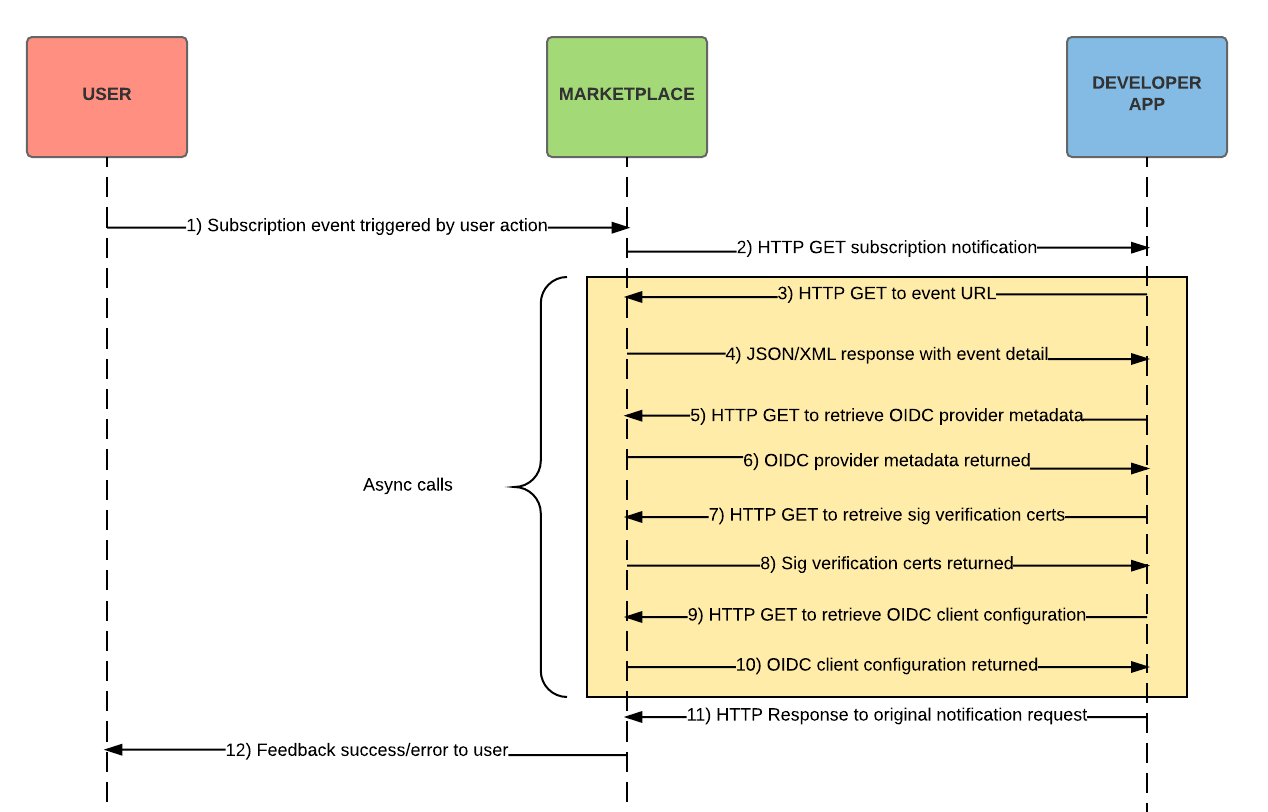
- An event is triggered by a customer action (for example, an application purchase).
- AppDirect sends a subscription event notification to the application vendor (developer). This event is uniquely identified by an event URL. See also step 11.
- The developer validates the OAuth-signature on the request, and can then read the event URL from the parameters to send an HTTP GET request for more information about this specific subscription event.
- AppDirect sends a JSON or XML response to the developer.
- The marketplace “baseUrl” sent in the SUBSCRIPTION_ORDER event is used to request the OpenID Connect provider metadata. See Example A—SUBSCRIPTION_ORDER event in the OpenID Connect authentication event examples topic.
📝 Note The metadata is located at
<marketplace_base_url>/.well-known/openid-configuration.
- Metadata is returned and is used to retrieve the issuer ID, endpoints, and signature verification certificates. See Example B—OIDC provider metadata in the OpenID Connect authentication event examples topic.
- The metadata contains a ‘jwks_uri’ parameter that points to the current set of signature verification certificates for that marketplace. Use this URL to request the current set of certificates.
- Signature verification certificates are returned (See Signature verification and key rotation to learn more, and see Example C—Signature verification certificates in the OpenID Connect authentication event examples topic for an sample response).
- The OpenID Connect client configuration is requested from the “oidcClient” endpoint included in the SUBSCRIPTION_ORDER event. This request is protected by the same OAuth key used in step 3. See Example A—SUBSCRIPTION_ORDER event in the OpenID Connect authentication event examples topic.
- The OpenID Connect client configuration is returned. See Example D—OIDC client configuration in the OpenID Connect authentication event examples topic.
- The developer responds to the original event notification (step 2), passing account and/or status information.
- This status information is used by AppDirect to provide feedback to the customer via the AppDirect UI.
Was this page helpful?
Tell us more…
Help us improve our content. Responses are anonymous.
Thanks
We appreciate your feedback!